Bitcoin Magazine

What Happens to Bitcoin When Quantum Computers Arrive?
Recent announcements in quantum computing have brought renewed attention to the question of how these advances could impact Bitcoin. In a newly published report, we provide an overview of the current state of quantum computing, the threat model for Bitcoin, and the next steps being considered. This post offers a summary of our key findings and recommendations. See the full report here.
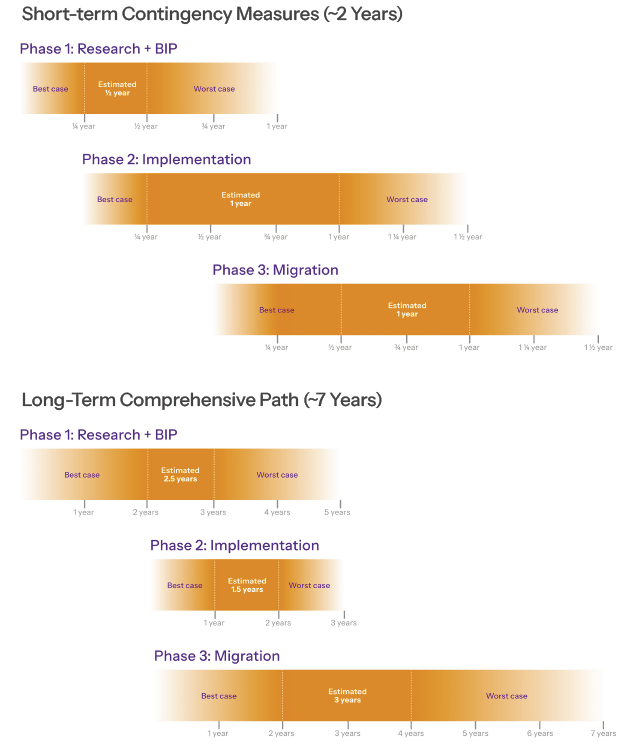
Timeline for Bitcoin Preparation to Quantum Computing
We outline a dual-track migration strategy for Bitcoin in response to the potential emergence of quantum computing.
- Long-Term Path: This comprehensive approach assumes that there is still a substantial window of time before quantum computing poses a practical threat. Drawing on the timelines of prior protocol upgrades such as SegWit and Taproot, we estimate that implementing a full quantum-safe transition could take approximately 7 years.
- Short-Term Contingency Path: This track serves as an emergency response in the event of a sudden breakthrough in quantum computing. It prioritizes a rapid deployment of protective measures to secure the Bitcoin network and could be executed in roughly 2 years.
In both scenarios, funds that are carefully managed, i.e., stored in hashed address types like P2PKH or P2WPKH without address reuse, are already protected from quantum attacks. However, spending those funds in a post-quantum secure way would require additional infrastructure, which is expected to be developed during the second phase of either timeline
Quantum Computers: When Are They Coming, and What Will They Be Capable Of?
If realized at scale, quantum computing could offer significant speed-ups for specific classes of problems by harnessing the principles of quantum mechanics. Of particular concern are cryptographically relevant quantum computers (CRQCs), machines capable of breaking the mathematical assumptions underlying modern cryptography. This includes algorithms like Elliptic Curve Cryptography (ECC), which is fundamental to Bitcoin’s security.
While quantum computing has been an active area of theoretical research for decades, significant engineering challenges remain in building large-scale quantum machines, especially CRQCs. To date, no quantum computer has surpassed classical supercomputers in solving commercially relevant problems, nor demonstrated the capabilities needed to threaten modern cryptography.
Estimated timelines for CRQCs
Technological progress is notoriously hard to predict, it rarely follows a linear path, and history offers many examples of sudden breakthroughs. In anticipation of potential shifts in the cryptographic landscape, several organizations have proposed timelines for transitioning cryptographic signatures.
One of the most prominent efforts comes from the U.S. National Institute of Standards and Technology (NIST), which has been leading the development of cryptographic standards. Their published recommendations highlight two key dates:
- By 2030, traditional encryption methods, such as ECDSA and RSA, should be phased out.
- By 2035, all cryptographic systems should transition fully to post-quantum algorithms.
The UK’s National Cyber Security Centre follows a comparable approach with a three-phase migration framework that aims to complete the transition to post-quantum cryptography by 2035. Other entities, such as the EU and China, are also actively working on post-quantum cryptography strategies, though they have not yet published formal timelines.
At the industry level, several leading companies, including Cloudflare, Signal, and Google, have begun adopting post-quantum cryptography. They are implementing hybrid signature schemes that combine traditional encryption methods with post-quantum algorithms, requiring an attacker to break both in order to compromise the system. Apple has also announced plans to transition to post-quantum cryptography. As PQC becomes an emerging industry standard, more companies are expected to follow suit.
What’s at Stake?
The financial stakes of the threat to Bitcoin are substantial. Fig 2 illustrates analysis revealing that approximately ~6.51 million bitcoin, worth over $700 billion at current valuations, and representing 32.7% of current supply, is quantum vulnerable. This includes funds held in addresses that have practiced address reuse, funds secured by inherently quantum-vulnerable script types, and funds that are vulnerable via public key exposure on forks of Bitcoin, such as Bitcoin Cash.
Bitcoin Threat Model: What Should We Be Worried About?
Quantum computing is expected to impact two key areas of Bitcoin: mining and transaction signatures. In quantum mining, the difficulty of combining the power of multiple machines gives a disproportionate advantage to large quantum miners, threatening decentralization. For transaction signatures, the risk is more direct, a CRQC could derive private keys from public keys, enabling theft of funds.
Importantly, the timelines for these two threats differ significantly. Building a quantum computer that can outperform modern ASIC miners presents a far greater engineering challenge than constructing one capable of breaking digital signatures. This is due, in part, to the low clock speeds of quantum processors, which are much slower than the highly optimized and specialized hardware used in Bitcoin mining and the lack of parallelization.
Signatures
A CRQC could break the assumption that it is infeasible to derive a private key from its corresponding public key under ECC based schemes, potentially allowing attackers to steal funds. In Bitcoin, ownership of a UTXO is proven by signing a transaction with the private key corresponding to a given public key. If a CRQC can derive that private key from the public key, it can falsely claim ownership and spend the funds.
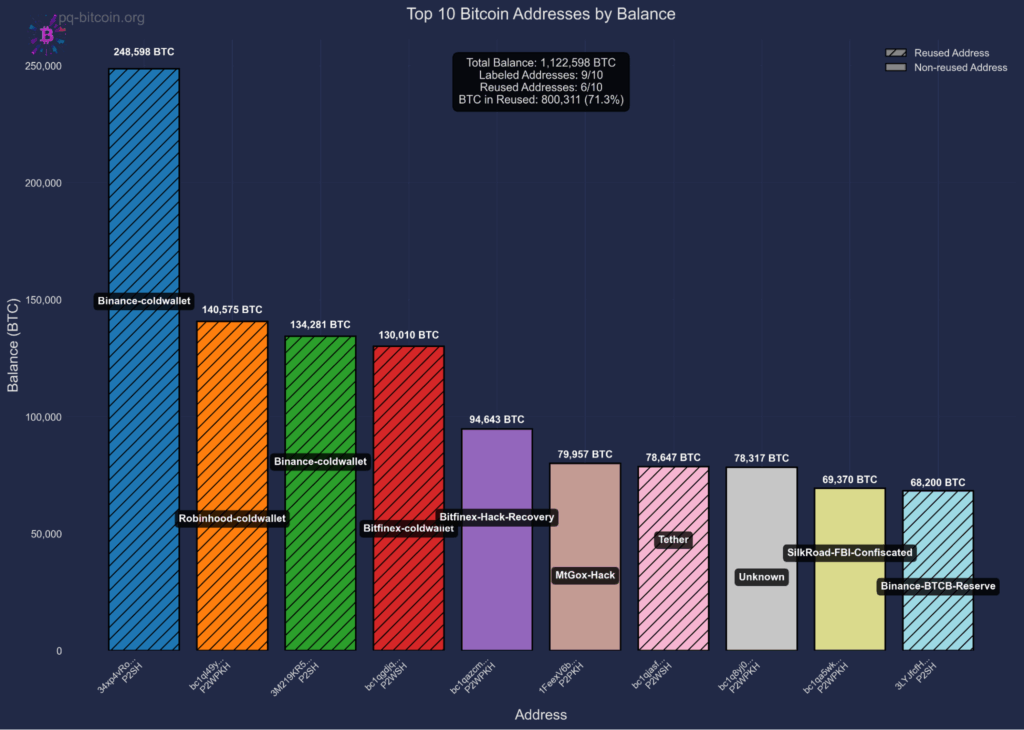
This leads to two distinct quantum attack scenarios. When spending from hashed addresses, public keys are revealed temporarily, giving attackers a brief window, typically minutes to hours, to derive private keys and steal funds, possibly through chain reorganization. In contrast, certain output types (P2PK, P2MS, P2TR) expose public keys permanently on-chain from the moment funds are received, giving attackers unlimited time to mount quantum attacks. Address reuse converts the temporary vulnerability of hashed addresses into permanent exposure, as public keys remain visible on-chain after the first spend. As shown in Fig 3, the most vulnerable targets are addresses that hold significant funds with exposed public keys such as institutional holdings that practiced address reuse.
Mining
Bitcoin mining is based on the principle that the probability of finding a valid block scales linearly with the amount of computational effort expended. Grover’s algorithm, a quantum search technique, offers a quadratic speedup for brute-force search. However, unlike classical mining, Grover’s algorithm is not easily parallelizable. This limitation could give a disproportionate advantage to entities with access to large-scale, centralized quantum hardware, potentially increasing mining centralization rather than broadening participation.
In addition to concerns about centralization, quantum mining could alter miners’ optimal strategies, potentially degrading chain quality, for example, by increasing the rate of stale blocks. A higher stale block rate can make certain attacks (such as selfish mining or double-spends) less costly and more feasible.
As noted earlier, building a quantum computer capable of outperforming modern ASIC miners is believed to be much farther off than developing CRQCs. As such, quantum mining is not an immediate concern and is unlikely to be a practical threat in the coming decades. Nevertheless, exploring Proof-of-Work mechanisms in a future quantum context remains a worthwhile research direction. Developing a better understanding of the potential risks and mitigation strategies would help the ecosystem prepare for a world where quantum mining becomes feasible.
Migration to Quantum Security: What are the main challenges?
Quantum-Secure Signatures
Quantum-secure cryptographic signatures have been studied for decades, but interest and progress have accelerated in recent years. This has led to the development of candidate protocols such as SPHINCS+, FALCON, and others. However, as a relatively young field, it has seen several proposed schemes initially believed to be secure but were later broken (e.g. SIKE), even by classical computers. While trust in the current candidates is growing over time, the field remains active and evolving.
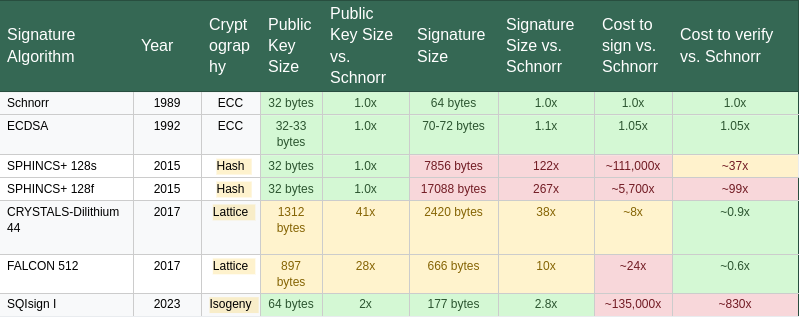
As detailed in Table 1, a significant limitation of post-quantum signature schemes is their substantially larger key and signature sizes, along with increased verification times, relative to classical algorithms such as ECDSA and Schnorr that are currently used in Bitcoin. To address this, some proposals suggest leveraging SegWit’s witness discount mechanism to reduce on-chain footprint. However, the best approach for integrating quantum-secure signatures into the protocol remains an open question. In addition to performance trade-offs, quantum-secure schemes do not yet support the full range of functionality provided by classical signatures, such as those relied upon in the Lightning Network and other applications. This area continues to be an active focus of research within the cryptography community, and further improvements are expected in the coming years.
Migration Pathways
If the Bitcoin community chooses to migrate vulnerable funds to quantum-resistant formats, a large number of UTXOs will need to be moved. Several approaches are under consideration, each making different tradeoffs. Some focus on enabling secure spending of hashed-address outputs without exposing the public key prematurely. Others propose mechanisms to limit or regulate the spending of UTXOs that are directly vulnerable to quantum theft. These strategies generally require changes to consensus rules, such as soft forks, and must also account for the practical challenge of moving a large volume of UTXOs, potentially taking 4 to 18 months even with sustained allocation of block space.
Philosophical Dilemma: Do we allow funds to be stolen?
The Bitcoin community faces a fundamental philosophical question: should quantum-vulnerable funds be made permanently unspendable (“burned”) or remain accessible to quantum computers (“stolen”)? This decision touches Bitcoin’s core principles of property rights, censorship resistance, and immutability. The burn approach treats quantum vulnerability as a protocol bug requiring a conservative fix, preventing wealth redistribution to those who win the CRQC race. The steal approach maintains that burning funds violates the property rights of their owners, effectively confiscating assets from those who may simply be unaware of the threat or unable to migrate in time.
The implications extend beyond philosophy to market dynamics. A coordinated burn would permanently remove millions of bitcoins from circulation, potentially increasing the value of remaining coins while providing market certainty. Allowing quantum theft enables massive wealth transfer to entities with quantum capabilities, potentially creating prolonged market uncertainty and volatility as funds are gradually drained. A decision on this matter is a defining moment for Bitcoin’s governance model, requiring the community to balance security imperatives against foundational principles of user sovereignty and non-intervention.
So, what’s next?
The arrival of CRQCs would mark a major shift across the digital landscape, placing much of today’s secure communication, authentication, and digital infrastructure at risk. While quantum computing is not yet a practical reality, preparations are underway to help ensure Bitcoin’s resilience against future developments. Research continues across both the cryptographic and Bitcoin communities to assess potential risks and explore practical responses. Our report highlights two areas that may warrant near-term attention: stopping address reuse and evaluating the trade-offs in the Burn vs. Steal discussion around exposed funds.
The window for proactive action is open now, though it may not remain open indefinitely. Staying informed about advances in quantum computing and cryptography is essential, as is studying potential mitigation strategies and their broader implications for the Bitcoin ecosystem. Ensuring Bitcoin’s long-term security in a post-quantum world requires thoughtful, deliberate work, starting now, so we can make well-informed decisions while time is still on our side.
This is a guest post by Clara Shikhelman and Anthony Milton. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
This post What Happens to Bitcoin When Quantum Computers Arrive? first appeared on Bitcoin Magazine and is written by Anthony Milton and Clara Shikhelman.



